
ESET Ireland wrote about Petya ransomware last year, a new variant massive cyberattack struck on June 27th. ESET LiveGrid technology detects the Petya malware as Win32/Diskcoder.C.
If you have a default install of any modern ESET product, ESET would protect against this threat. Additionally, any ESET product with network detection would protect from the SMB spreading mechanism – EternalBlue proactively.
Government computers, banks and airports in Ukraine are reported to have been hit by Petya.A ransomware. Also confirming a security incident is Ukrenergo, a Ukrainian state power distributor, Reuters has noted. The global shipping company Maersk is reported to have been hit by a ransomware attack and the Russian state-run Rosneft oil company reports a ‘major’ cyberattack. In the US, Merck, one of the largest pharmaceutical companies in the world has been hit as well. Reports of infections are also coming from Spain, Britain, India and France.
ESET researcher Robert Lipovsky comments:
“Today, early afternoon (CEST), ESET researchers have begun investigating another massive global ransomware epidemic following the WannaCry and XData/AES-NI outbreaks. The ransomware appears to be a version of Petya. If it successfully infects the MBR, it will encrypt the whole drive itself. Otherwise, it encrypts all files, like Mischa.
For spreading, it appears to be using a combination of the SMB exploit (EternalBlue) used by WannaCry for getting inside the network and then spreading through PsExec for spreading within the network. This dangerous combination may be the reason why this outbreak has spread globally and rapidly, even after the previous outbreaks have generated media headlines and hopefully most vulnerabilities have been patched. It only takes one unpatched computer to get inside the network, and the malware can get administrator rights and spread to other computers.
The outbreak appears to have started in Ukraine, where reports indicate that the financial sector, energy sector and numerous other industries have been hit. The scope of the damage caused to the energy sector is not yet confirmed, and there has been no reports of a power outage – as was the case previously with the infamous Industroyer malware.”
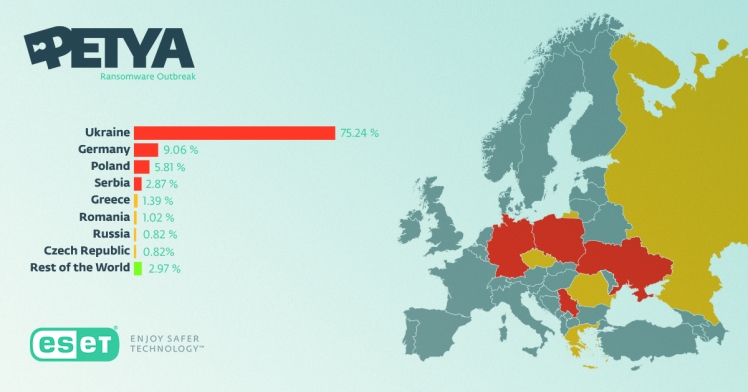
We see thousands of attack attempts at unique users. The statistics below are percentages from 100% of all detections – detections at unique users (meaning machines):
| 75.24% | Ukraine |
| 9.06% | Germany |
| 5.81% | Poland |
| 2.87% | Serbia |
| 1.39% | Greece |
| 1.02% | Romania |
| 0.82% | Russia |
| 0.82% | Czech Republic |
| 0.50% | Italy |
| 0.42% | Estonia |
| 0.23% | Israel |
| 0.20% | Belarus |
| 0.16% | Netherlands |
| 0.15% | Hungary |
| 0.12% | Kazakhstan |
| 0.12% | Latvia |
| 0.12% | Cyprus |
| 0.10% | Spain |
| 0.09% | United Kingdom |
| 0.09% | United States |
| 0.09% | Slovakia |
| 0.09% | Belgium |
| 0.09% | Lithuania |
| 0.07% | People’s Republic of China |
| 0.06% | France |
| 0.03% | Argentina |
| 0.03% | Brazil |
| 0.03% | Taiwan |
| 0.03% | Turkey |
| 0.03% | South Africa |
| 0.01% | Thailand |
| 0.01% | Viet Nam |
| 0.01% | Georgia |
| 0.01% | Korea |
| 0.01% | Kuwait |
| 0.01% | Morocco |
| 0.01% | Azerbaijan |
| 0.01% | Iran |
| 0.01% | Australia |
What is Petya?
The older variants of Petya, that ESET analysed, revealed that the ransomware causes the “blue screen of death” after successful infiltration of Windows, thus forcing the victim to restart his/her machine. If the user does so, instead of loading the operating system he/she will only be displayed a ransom demand (previously for 0.99 bitcoin/$431 but this may vary).

To accomplish this, it modifies the master boot record (MBR) to run the ransomware code instead of the system code. It then encrypts the master file table (MFT), which describes all files on the volume; by basically telling the system where the files are located and what the directory structure looks like.

ESET analysis of the older version has shown, that Petya (despite the claim in the ransom message) is not encrypting the files themselves on the computer’s disks, only the file table. This (gap) allows users to recover files with some of the recovery tools available (although this might lead to some costs).
However, the Petya malware variant used in the latest attacks has yet to be properly analysed, to determine how much damage it does this time around. The latest variant appears to be using the same SMBv1 vulnerability, that the WannaCry ransomware used to massively infect computers all over the world.

An image, similar to the one witnessed by WannaCryptor victims, reportedly showing the ransomware message is making the rounds online, with one from Group-IB showing the following message (paraphrased):
“If you see this text, then your files are no longer accessible, because they have been encrypted … We guarantee that you can recover all your files safely and easily. All you need to do is submit the payment [$300 bitcoins] and purchase the decryption key.”
To ensure the highest level of protection against this threat, follow the steps below:
- Home Users: Perform a Product Update
Business Users: Send an Update Task to all Client Workstations - Make sure that you have all current Windows Updates and patches installed.
For more information about this threat, see our Customer Advisory
Update (June 28 – 15:00 CEST): ESET researchers have confirmed that further affected systems had access to Ukraine networks through VPN. Presently, it has not been seen in the malware a functionality to spread outside of the LAN network.
Update (June 27 – 23.34 CEST): Shutting down the computer and not booting again could prevent the disk encryption, though several files can be already encrypted after the MBR is replaced and further infection through the network is attempted.
Update (June 27 – 22.28 CEST): Paying is no longer possible as the email to send the Bitcoin wallet ID and “personal installation key” has been shut down by the provider. Thus, people shouldn’t pay for the ransom as they will not be able to receive the decryption key.
Update (June 27 – 21.20 CEST): ESET researchers have located the point from which this global epidemic has all started. Attackers have successfully compromised the accounting software M.E.Doc, popular across various industries in Ukraine, including financial institutions. Several of them executed a trojanized update of M.E.Doc, which allowed attackers to launch the massive ransomware campaign today which spread across the whole country and to the whole world. M.E.Doc has today released a warning on their website: http://www.me-doc.com.ua/vnimaniyu-polzovateley
Stay tuned for further developments and check out our other ransomware-related blogs!
What is ransomware and should you pay up?
More info about Petya ransomware.
Click here to read how to deal with ‘wannacry’ ransomware?
Read about Android ransomware.
Learn about ransomware on Macs.
by Urban Schrott, ESET Ireland
