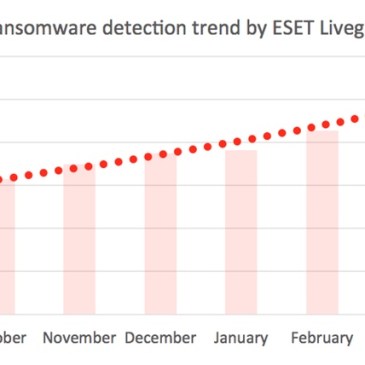
ESET releases new decryptor for TeslaCrypt ransomware
Have you been infected by one of the new variants (v3 or v4) of the notorious ransomware TeslaCrypt? If your encrypted files had the extensions .xxx, .ttt, .micro, .mp3 or were left unchanged, then ESET has good news for you: we have a decryptor for TeslaCrypt. We have been covering this malware for a few … More ESET releases new decryptor for TeslaCrypt ransomware