The death of Osama bin Laden has gone viral with blogs, social media and search engines pumping terabytes of rumour, innuendo and conspiracy theories at the speed of light, along with the occasional kilobyte of truth. That was the state of global malware map after the death of Osama bin Laden that came in early May. Nigerian letters involving Libya was yet another top scam for the past few weeks. For the month of April, ESET’s ThreatSense.Net statistics once again put INF/Autorun in top spot of global malware statistics (6.62%), followed by Win32/Conficker (3.76%) and Win32/PSW.OnlineGames (2.02%).

As the number of people searching for pictures and videos of bin Laden’s execution skyrocketed, the criminal syndicates which perform “black hat” search engine optimisation have exploded as well. The result is a great number of malware-laden sites tricked out to perform all sorts of tricks to get them returned as the first results in search engine results. While such criminal activities have become the norm, are highly automated and otherwise not worthy of interest, the sheer amount of search activity has unleashed a tidal wave of scams and malware.
Global malware thrives on the demise of a global terrorist and ESET is also registering a similar upsurge on Facebook. It’s easy to see why: With over five hundred million active users, Facebook would rank just behind China and India as the third-most populated country in the world, if it happened to be a country. As researchers at ESET Latin America report, criminals are using social engineering to bypass Facebook’s own security measures against malicious JavaScript code by tricking people into copying and pasting it directly into their web browser’s address bars.
Libyan war also provided ample inspiration for cyber-criminals in the last few weeks. ESET researchers are reporting upsurge in Nigerian letter scams which cost gullible PC users billions of dollars every year. Just recently a model Nigerian letter appeared, using the Libyan crisis as bait and “government funds” as a hook. According to 419hell.com website which explores these types of cyber-threats, someone falls for this type of scam every 44 seconds.
Europe, Middle East and Africa Threatscape: Win32/Autoit makes headways
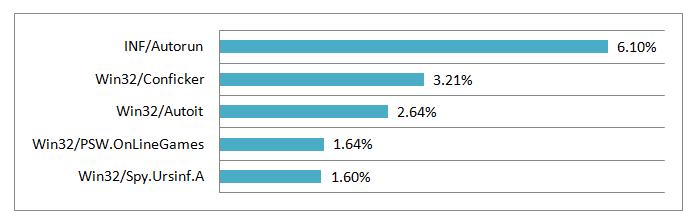
European threat statistics propelled a newcomer, Win32/Autoit to top three, with a 2.64% share (1.1% globally). Win32/Autoit is a worm that uses primarily removable media to disseminate; with some of it variants spread also through Instant Messaging. It may arrive as a downloaded file from a malicious website or may also be dropped by another malware. Once executed, it downloads additional threats or variants of itself. With 8.13% percent it was a top threat in Turkey.
Moreover, INF/Autorun was yet again the top malware in most European countries (European average of 6.1%) and the whole EMEA region for the month of April. It connotes a variety of malware using the autorun.inf file as a way to compromise a PC. It was the most widespread type of malware in South Africa (11.13%), Ukraine (6.25%), Israel (6.25%), Croatia (5.68%), Austria (4.68%), Hungary (4.38%), Italy (4.11%) and Belgium (4.0%) among others. Win32/Conficker moved to second slot (3.21% in Europe), topping the threat landscape in Bulgaria, where it accounted for 7.72% of all infiltrations. Win32/PSW.OnLineGames represents a family of trojans used in phishing attacks aimed specifically at gamers. In April it was among the most widespread malware in Poland with a share of 5.7% (1.64% in Europe overall).